Now Reading: Transforming Physical Substation Security
-
01
Transforming Physical Substation Security
Transforming Physical Substation Security
This is a sponsored article brought to you by POWER Engineers, Member of WSP.
Digital transformation is reshaping industries across the globe, and the power delivery sector is no exception. As demand for reliable and efficient energy supply continues to grow, the need to modernize and optimize operations becomes increasingly critical. By leveraging digital tools and technologies, utilities are unlocking unprecedented opportunities to enhance precision, efficiency and resilience throughout the power delivery value chain—from generation to distribution.
However, while digitalization offers transformative potential, the power delivery industry continues to grapple with substantial technical and operational challenges. Many utilities still operate with legacy or manual security protocols that rely on reactive rather than proactive strategies. The slow pace of technology adoption further compounds these issues, increasing the vulnerability of critical assets to inefficiencies, downtime and physical threats. Overcoming these obstacles requires a strategic shift toward innovative solutions that drive measurable improvements in safety, reliability and operational optimization.
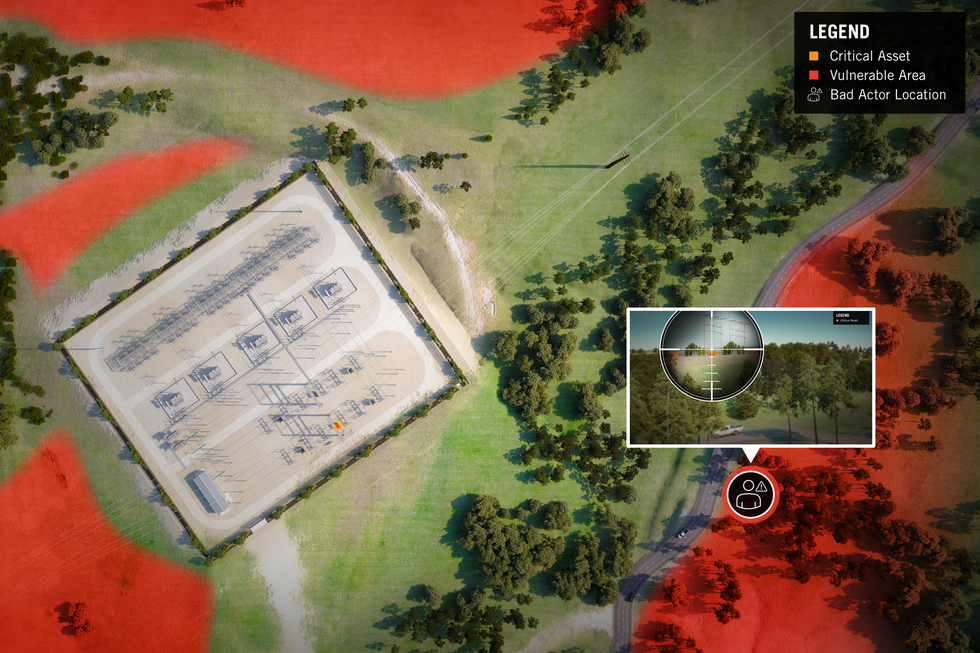
Meerkat takes the guesswork out of substation security by integrating high-fidelity data with real-time 3D mitigation modeling. This sophisticated approach identifies all line-of-sight vulnerabilities, and delivers robust protection for critical infrastructure in an increasingly complex threat landscape.Video: POWER Engineers, Member of WSP
The Need for Digital Transformation in Physical Security
Physical attacks on substations are becoming increasingly prevalent and sophisticated. As technology evolves, so do the bad actors that are trying to take down the grid. Many mitigation methods are no longer sufficient against modern methods of attack. These facilities, which are crucial to keeping the grid operational, must be able to comprehensively assess and adapt to new threats. Digital transformation is the key to this goal.
 Physical breach events, defined here as physical attacks, vandalism, theft and suspicious activity, accounted for more than half of all electric disturbance events reported to the United States Department of Energy in 2023. POWER Engineers, Member of WSP
Physical breach events, defined here as physical attacks, vandalism, theft and suspicious activity, accounted for more than half of all electric disturbance events reported to the United States Department of Energy in 2023. POWER Engineers, Member of WSP
Traditional Methods Fail to Meet Modern Demands
Conventional site analysis methods in power delivery are often inefficient and prone to inaccuracies, particularly at substations, where the shortcomings can lead to significant vulnerabilities.
Physical site walkthroughs to identify areas of vulnerability, for example, are inherently subjective and susceptible to human error. Compounding matters, safety concerns in high-voltage environments, coordination challenges and access restrictions to areas not owned by the substation can result in incomplete assessments and evaluations fraught with delays.
Static analysis is also limited by outdated or erroneous publicly available data, hindering precise assessments and delaying decision-making processes. For instance, assets captured in publicly available data may misrepresent recent construction near the site, which may create new lines of sight to critical assets.
Meerkat, developed by POWER Engineers, Member of WSP, leverages advanced technology to enhance threat assessment accuracy, significantly reducing assessment times, lowering mitigation costs and improving overall protection at substation facilities.
The Vulnerability of Integrated Security Analysis (VISA) method attempts to address some of these shortcomings by leveraging expert collaboration. Yet, it too has limitations—expertise variability among participants can lead to unrepresented perspectives, and reliance on static drawings and resources hampers effective visualization during sessions.
In contrast, some utilities opt for no analysis at all, erecting perimeter walls around facilities without pinpointing specific vulnerabilities. This approach often results in overbuilding and overspending while potentially leaving critical assets exposed due to overlooked threats from neighboring structures or terrain features.
Communication silos between stakeholders can also exacerbate these inefficiencies.
It’s Time to Transform: Embrace Digital Solutions
Emerging tools and technologies have the ability to address the longstanding inefficiencies in physical substation security.
Enhance Precision and Efficiency
Integrating cutting-edge technologies such as real-time data analytics and remote sensing, for example, can significantly enhance the precision and efficiency of security assessments. These tools provide dynamic insights into potential vulnerabilities, enabling proactive measures that adapt to emerging threats.
Prioritize and Optimize Resources
Transitioning from subjective assessments to data-backed evaluations ensures that decisions are grounded in accurate information rather than intuition alone. Robust datasets allow for thorough risk analyses that prioritize high-impact vulnerabilities while optimizing resource allocation.
Implement Scalable Solutions
Embrace flexible solutions capable of scaling with evolving infrastructure requirements or regulatory changes over time. This adaptability ensures continued relevance amidst shifting industry landscapes driven by technological advancements or policy shifts.
Where to Start
To solve the insufficiencies found within conventional site assessment methodologies, POWER Engineers, Member of WSP, designed a transformative threat assessment tool called Meerkat. Meerkat harnesses high-quality data and advanced modeling techniques to deliver comprehensive vulnerability assessments customized to each unique facility. It is offered alongside an industry-leading team of experts who can help break down costs, explore alternative mitigations and address operational concerns.
Meerkat revolutionizes physical substation security by offering a more accurate and thorough analysis compared to conventional approaches. It mitigates the risk of human error inherent in manual inspections and overcomes access limitations through advanced remote sensing capabilities. Additionally, Meerkat facilitates seamless collaboration among stakeholders by providing dynamic, easily interpretable visualizations that enhance communication and decision-making processes. Analyses can even be performed in a secure, online workshop, allowing subject matter experts to skip the travel delays and jump right into the action.
By using Meerkat in substation security projects, utilities can transition from reactive to proactive strategies that anticipate and counter potential vulnerabilities before they are exploited. This shift not only ensures compliance with regulatory standards but also aligns security enhancements with financial objectives, ultimately safeguarding both assets and investments in a rapidly changing technological landscape.
How it Works
 The Meerkat assessment features real-time mitigation modeling, optimizes camera placement, and identifies all vulnerabilities that could be exploited by malicious actors.POWER Engineers, Member of WSP
The Meerkat assessment features real-time mitigation modeling, optimizes camera placement, and identifies all vulnerabilities that could be exploited by malicious actors.POWER Engineers, Member of WSP
Step One: Data Collection
Meerkat starts with data collection. When pre-existing data of the site is available and of good quality and accuracy, it can be used for this process. However, when there is not sufficient data available, the Meerkat team collects its own high-fidelity data of the study area. This includes the substation facility, property and all surrounding terrain and infrastructure within an established radius of concern.
Step Two: Build a Model
Next, the high-quality data is transformed into an interactive 3D model in a virtual environment. The model is so accurate that it can facilitate virtual site visits. Users can navigate around the substation environment by clicking and dragging on screen and can visualize the site from any point ranging from a bird’s-eye view to the perspective of a potential bad actor looking into the station.
Step Three: Test Mitigations in Real Time
This interactive model serves as a virtual sandbox where mitigation strategies can be tested in real time. It can comprehensively and objectively map all line-of-sight vulnerabilities—big and small—that a bad actor might use to attack critical components. Then, existing or proposed mitigation strategies, if available, can be tested and validated within the system. This stage is great for testing what-if scenarios and seeing how multiple mitigations interact if combined before construction even comes into play.
Step Four: Find the Best-Cost Solution
POWER’s team of industry-leading experts use their knowledge to guide iterative solutions that bring substation owners and operators closer to the best-cost solutions for their substations. Sometimes moving or changing the height of a proposed wall is all it takes to drastically improve protections without drastically changing the price. A built-in cost estimator can also give a rough idea of how material costs change as the design does.
The Benefits of Using Meerkat
Meerkat is an industry-leading technology that offers unparalleled benefits in conducting thorough vulnerability assessments for critical assets at substations. By leveraging sophisticated algorithms and high-quality data, Meerkat delivers precise evaluations that pinpoint potential weaknesses with exceptional accuracy. This comprehensive approach means that every aspect of a substation’s physical security is meticulously analyzed, leaving no stone unturned.
Enhanced Efficiency
One of the key advantages of Meerkat is its ability to significantly enhance efficiency in the assessment process. This not only reduces the time and resources required for site assessments but also ensures consistent and reliable results.
Meerkat also allows an evaluation and design process that can sometimes take months of back-and-forth communication to happen in just a handful of hour-long workshops.
Improved Accuracy
Accuracy is another hallmark of Meerkat, as it eliminates the guesswork associated with human-based evaluations. By leveraging advanced modeling techniques, Meerkat provides actionable insights that empower utilities to make informed decisions regarding security upgrades and mitigations. This precision facilitates proactive risk management strategies, allowing stakeholders to address vulnerabilities before they manifest into tangible threats.
Ultimately, by improving both efficiency and accuracy in vulnerability assessments, Meerkat enables better decision-making processes that enhance overall risk management. Utilities can confidently implement targeted security measures tailored to each site’s unique needs, ensuring robust protection against emerging threats while optimizing resource allocation. In a landscape where rapid technological advancements challenge conventional practices, Meerkat stands as a vital tool for safeguarding critical infrastructure with foresight and precision.
Get Started
Any entity interested in learning more about Meerkat and its applications can request a free demonstration from our team of experts at meerkat.powereng.com.